Network Access Control List (NACL)
Network Access Control List aka NACL aka Network ACL is like a firewall for filtering traffic from and to subnets. It is an optional layer of security. This means there is no need to create a new network access control list and associate it with the subnet. AWS creates default network ACL in all VPCs. In this blog post, I am going to tell you about, default network ACL, subnet association, adding inbound and outbound rules, how rules are evaluated, etc.
Default Network ACL
- AWS creates it inside every VPC.
- Allows everything outbound and everything inbound.
- When you create a subnet in a VPC then default NACL is associated to that subnet.
Rules
- Allows to define either allow or deny rule.
- Every rule has a number associated with it.
- Every NACL has a rule with number as asterisk (*). This rule can not be modified. If there is no match then this rule is applied.
- A network ACL has separate inbound and outbound rules, and each rule can either allow or deny traffic.
- To define a rule requires:
- Rule number: e.g. 100, 110, etc.
- Type: e.g. SSH
- Protocol: e.g. HTTP, ICMP, etc
- Port range: e.g. 80
- Source: applies only to Inboud Rule. e.g. CIDR range
- Destination: applies only to Oubound Rule. e.g. CIDR range
- Allow/Deny
- Network ACLs are stateless, which means that if request is allowed via Inbound rule then response should be allowed via Outbound rule (vice versa).
- Inbound and Outbound rules must be present in order to allow perticular traffic.
- Rule number range starts from 1 to 32766.
- It is recommended to add a rules in increments of either 10 or 100. This allows to add new rules where you need to later on.
- Both Inbound and Outbound rules are configured, below is the screenshot from AWS console:
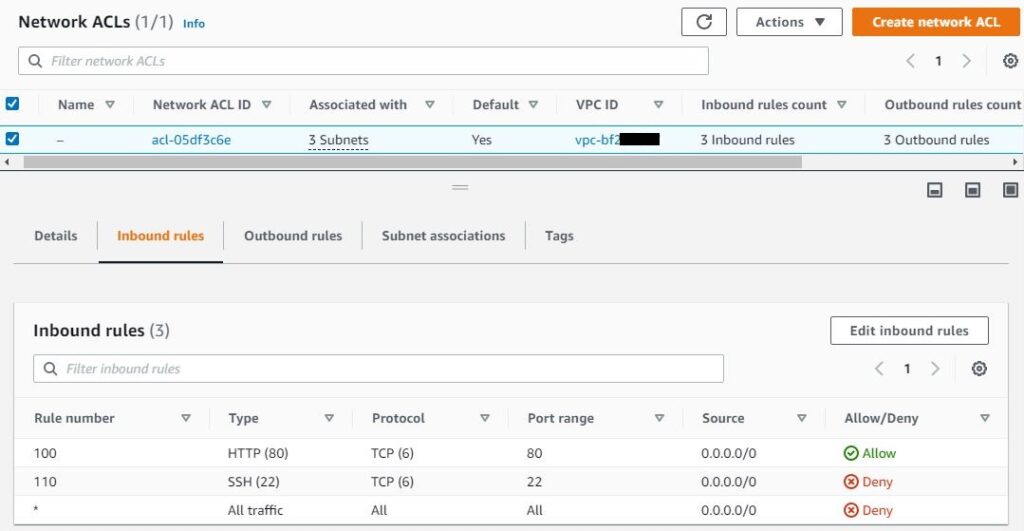
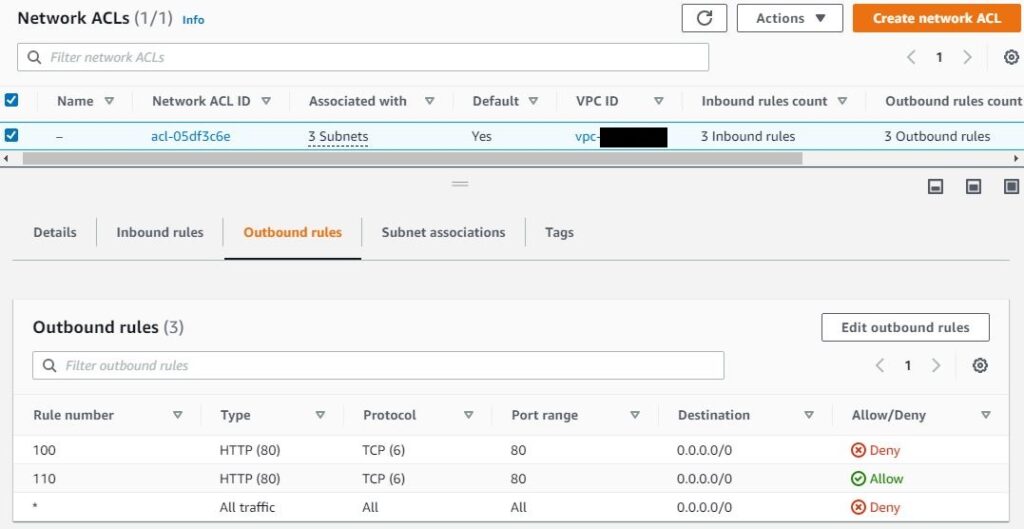
Rule evaluation
- Rule evaluation starts from the lowest number.
- Higher precedence with a lower number. For example, rule with number 100 has higher precedence over rule number with 110
- When there is match then further rules are no evaluated.
- In the above image “Network ACL Outbound Rules“
- There are two rules.
- Rule number 100 is denying the HTTP(80) traffic from all IPs.
- Rule number 110 is allowing the HTTP(80) traffic from all IPs.
- As stated above, when there is matching rule found no futher evaluation happens.
- For this scenario, rule 100 is matched. If we modify the rule number 110 to less than 100. Let’s say 90 then “all the HTTP(80) traffic from all IPs will be allowed”. The deny rule number 100 won’t be considered.
Key points to remember
- Additional layer of firewall, controls subnet traffic.
- Only default NACL allows everything outbound and inbound. Custom NACLs deny everything outbound and everything inbound.
- You can associate a NACL to many subnets but remember one subnet has one NACL associated.
- Network ACLs are stateless. Separate Inbound and Outbound rules have to be defined.
