Security Groups vs Network Access Control Lists
Network Access Control List aka Network ACL is a way to control the inbound and outbound traffic of one or more Subnets. It acts as Firewall for subnets. It provides the additional layer of defense if Security Groups are too permissive. On the other hand, the Security Group is also used to control the traffic. The main difference is, Security Group is used at the instance level i.e. inside the subnet. Apart from this, there are more differences like rule evaluation, stateful vs stateless. We will see all the major differences shortly.
First, we will see all the differences and then followed by a detailed explanation.
| Security Group | Network Access Control List |
|---|---|
| 1. Operates at Instance Level | 1. Operates at the Subnet level |
| 2. Supports allow rules only | 2. Supports allow rules and deny rules |
| 3. Rules are not assigned any numbers | 3. All Rules are assigned numbers (e.g. 100, 110, etc.) |
| 4. Evaluate all the rules and decide either to allow or deny | 4. Rules are evaluated according to ascending order. The first matched rule decides either allow or deny. When match found no further evaluation of rules |
| 5. No concept of the default rule. No rule then deny everything | 5. Default rule with a wildcard (*). Which is by default deny everything |
| 6. Attach SG either at the time of launching an instance or after an instance is launched | 6. Implicitly applies to all the subnets. As there is a default Network ACL created in every VPC |
Detailed explanation
Refer to the point from the above table (numbers)
1. Operated at
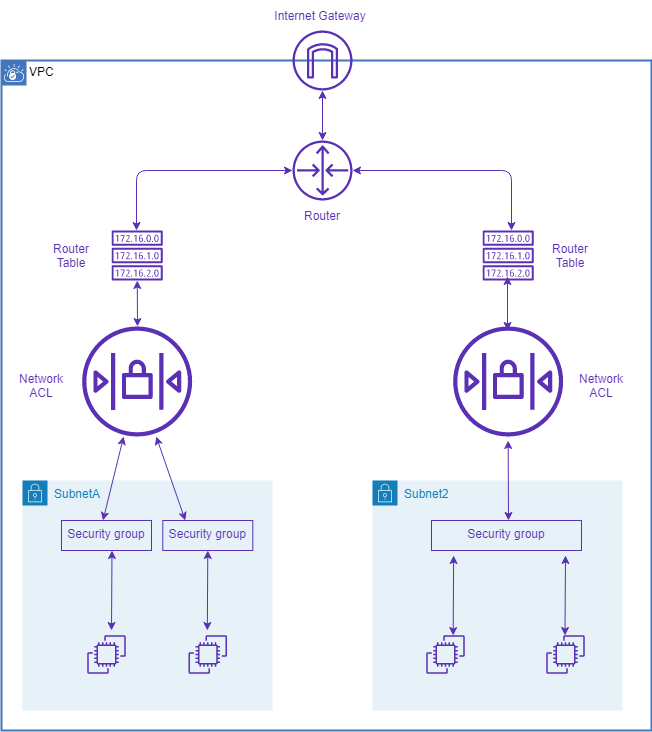
- Network ACLs are associated with Subnet(s). Additional layer of defense outside of Subnet
- Security Groups are attached to the EC2 instance(s). Controls which traffic is allowed to the instance, inside the Subnet.
2. Supported rules – Allow, Deny
3. & 4. Rules – Numbers – Evaluation
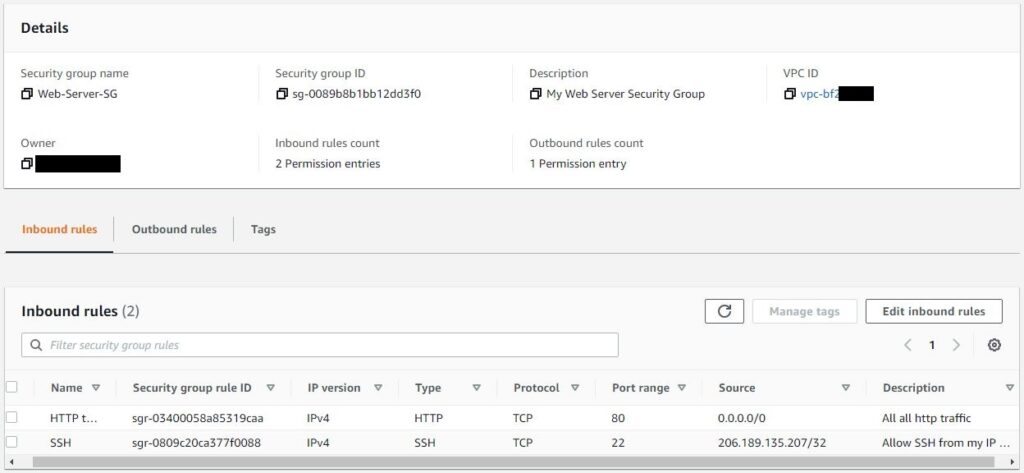
- Security Groups
- Either allow or deny a traffic is decided by evaluating all the rules present in the Security Group.
- As a reason rule numbering is not required
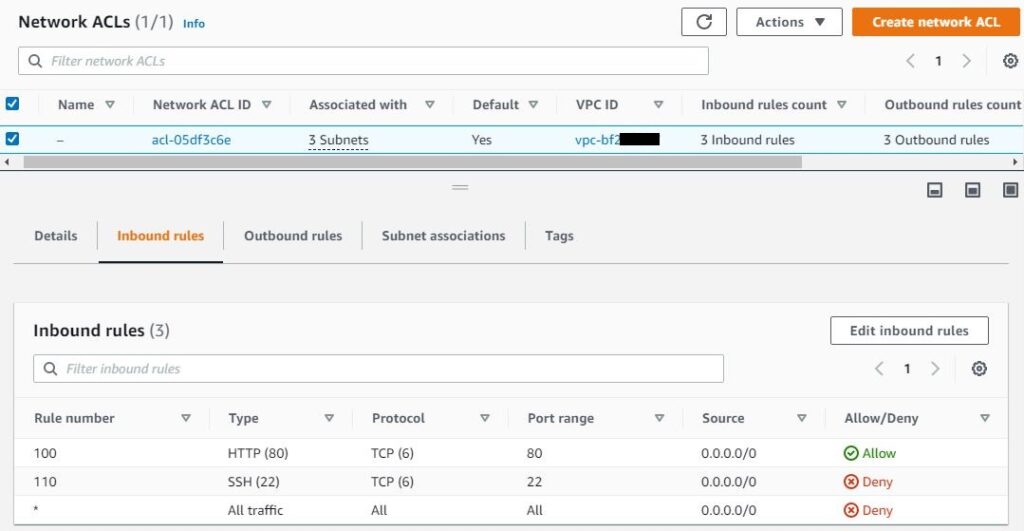
- Network ACLs
- Defines the rules with numbers.
- Refer explanation point 2 image.
- Rule evaluation starts from the lowest number. If the match is found then further rules are no evaluated. For more on Network ACL rules, here is the NACL blog post.
5. Default Rule
- Security Groups
- Inbound or Outbound rules can be empty.
- Only defines allow rules.
- There is no concept of deny rule.
- If a rule is specified then it is by default allowing some traffic.
- Network ACLs
- There is always default rule present, which is match all (*)
- Default rule deny all traffic
- Refer Network ACL image from point 2. Check at the bottom, there is a default rule.
6. Association
- All the subnets are associated to the default Network ACL.
- You can always create a custom Netwrok ACL and associate your subnets to that ACL.
- Security Groups are required to be explicitly attached to an instance at launch or after launch.
